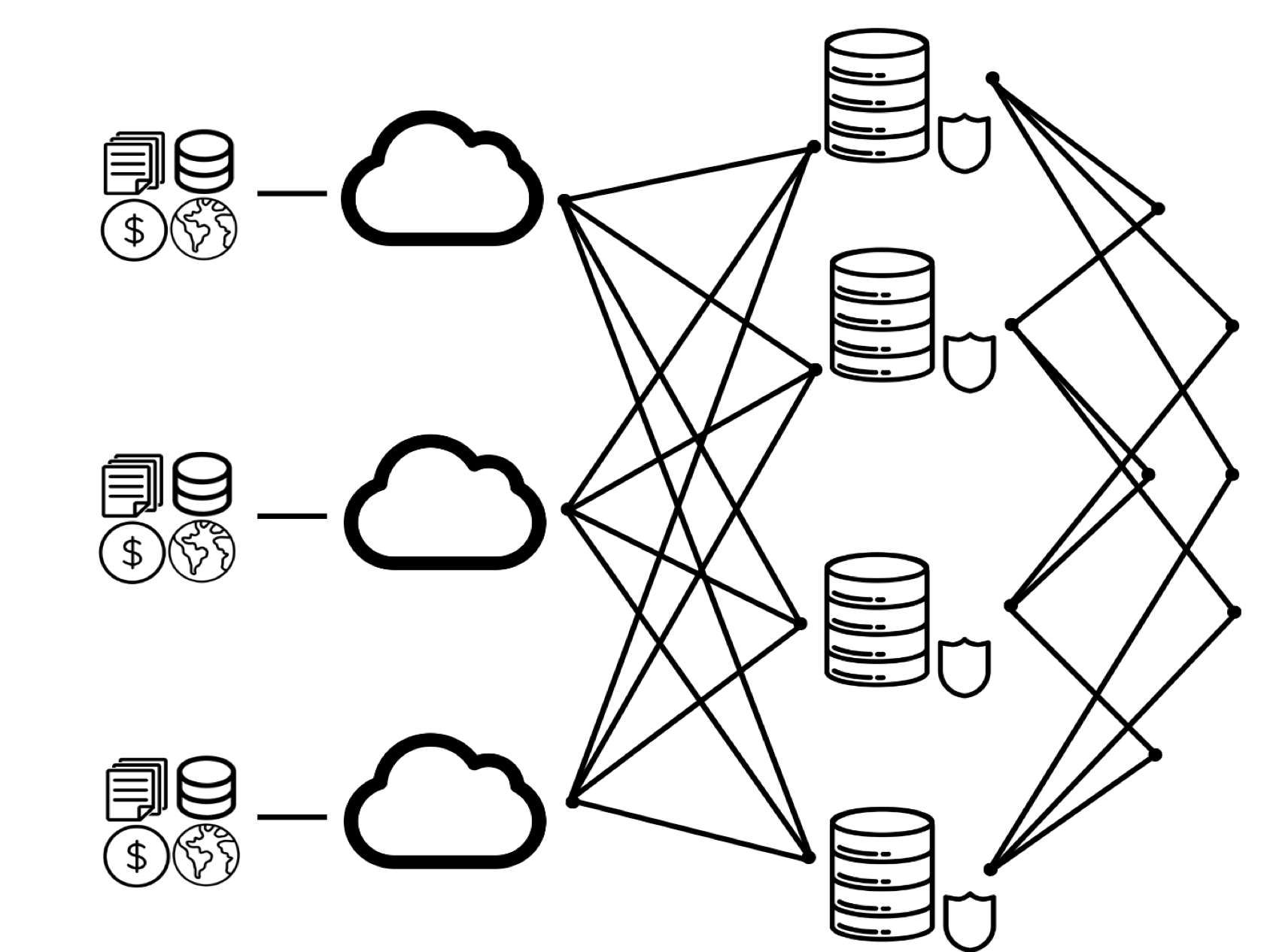
Thissl provides a decentralized data center architecture that, as the network grows, becomes more stable, scalable, and secure.
Thissl Hardware Specs
Thissl Hardware Specs
Entry Node: Intel Core i3 10100F / 3.6 GHz processor, 2 x Crucial 8GB PC4-25600 3200MHz DDR4, 2TB 2.5inch 7mm SSD
SMB Node: 1U Appliance 265W PS 0 0 (4*2.5), LGA1700 Socket Motherboard mini ITX formfactor Motherboard, Intel Core i5-13500, 14 P+E Cores - 1.80 GHz Base, 4.80 GHz Max Turbo, 2 x 16GB PC4-25600 3200MHz DDR4, 1.92TB Micron 5400 PRO Series 2.5" SATA 6.0Gb/s Solid State Drive, 3.84TB Micron 5400 PRO Series 2.5" SATA 6.0Gb/s Solid State Drive
Enterprise Node: 2U - 12x 3.5" Hot-swap SAS/SATA, Intel Xeon Silver 4309Y Processor 8-Core 2.8GHz, 8 x 16GB PC4-25600 3200MHz DDR4 ECC RDIMM, 2 x Sam SATA PM893 2.5 480GB SSD, 2 x 2.0TB Kioxia XG8 M.2 PCIe 4.0 x4 NVMe Solid State Drive, 12 x 3.84TB Solidigm SSD D3-S4520 Series 2.5" SATA 6.0Gb/s Solid State Drive, Broadcom HBA 9500-8i SAS3/SATA/NVMe 8-Port Tri-Mode Host Bus Adapter - PCIe 4.0 x8, Dual Intel 10-Gigabit Ethernet (RJ45)
Privacy
Encryption
Blockchain SHA-256 encryption level protects against reverse engineering data making it impossible to access against brute force attacks. The network takes all requests, data, identities, and keys and encrypts them at the highest standard available at the client level, leaving no room for exposure.
Sharding
The division of encrypted data on a network creates both capacity for efficient redundancy, lighting transportation, and increased data security across the network.
Economics
Economics
To prevent any node from becoming malicious and exposing, copying, or failing to respond to data requests, economics are put into place to discourage bad acting and incite good acting on the network.
Perfomance
Through combining an edge network, interconnected node communication pathways, and sharding of data into small files allows for data to be transported, stored, and called at extremely high efficiency. Each node increases the network's compute capacity in its entirety.
Using an embedded firewall within the OS of each node allows the creation of a processing layer for users entirely in layer2. A unilateral layer2 decreases dependency on layer1 pipes while placing the processing, security, and serving of data within the same network layer as the end user.
Reliabilty
A decentralized computing network is always available and accurate in its internal referencing (ledgers, records, etc). A proprietary network protocol is put in place, allowing simultaneous multi-casting of data packets across the network of nodes. This allows users to perform in a lossless capacity within the network. Nodes transmit and receive all data across all available network mediums installed on the board of the node. Nodes have ethernet, fiber, wi-fi, LTE, TVWS, and usb-a and c available for network operability on the node itself. All processed packets are transmitted across all network hardware options on the node, and the first packet delivered wins.
